The SAS Viya LTS 2021.2 release supports application multi-tenancy. This 3-part series reviews how authentication can be configured.
SAS Viya 2021.2 OIDC with Multi-Tenancy
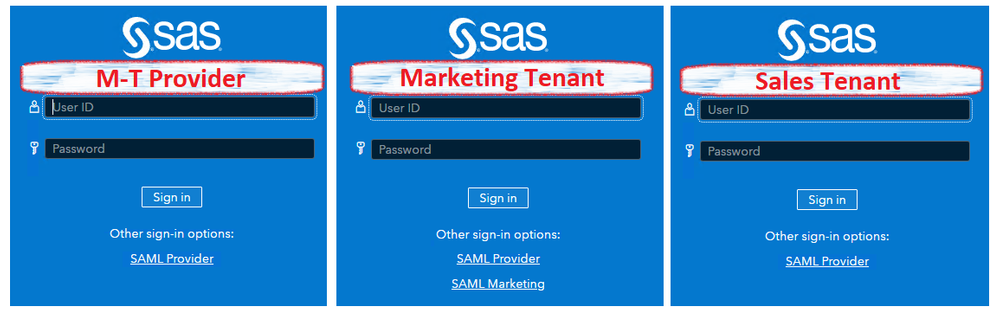
In this post, we look at configuring OpenID Connect (OIDC) authentication in a multi-tenant (M-T) environment. The SAS Viya configuration of OIDC authentication could be performed in the M-T provider and apply to all tenants or could be configured in one or more individual tenants and only apply to that tenant. For this post, we configure ODIC for the M-T provider and the marketing tenant.
The third-party OIDC Identity Provider, such as Azure Active Directory, has three key properties. These are:
- The Relying Party ID or Client ID – which is a unique name for the SAS Viya instance in the third-party OIDC Identity Provider.
- The Relying Party Secret or Client Secret – which is a shared secret between the SAS Viya instance and the third-party OIDC Identity Provider used to authenticate SAS Viya to the OIDC Identity Provider.
- One or more Redirect URIs – these are normally fully qualified URLs registered with the third-party OIDC Identity Provider. Only authentication requests coming from these registered URLs are valid.
SAS Viya 2021.2 SAML with Multi-Tenancy
In this post, we look at configuring SAML authentication in a multi-tenant (M-T) environment. There are two parts to the SAS Viya SAML configuration. The first part configures SAS Logon Manager as a SAML Service Provider and is configured with the settings under sas.logon.saml. The SAML Service Provider settings are configured only in the M-T provider.
The second part of the SAS Viya SAML configuration is the link to the third-party SAML Identity Provider, and is configured with the settings under sas.logon.saml.providers. The sas.logon.saml.providers settings can be configured for the M-T provider and apply to the provider and all tenants. Or the sas.logon.saml.providers settings can be configured for an individual tenant and apply to that tenant only.
For this post, we configure the sas.logon.saml settings in the M-T provider. Then we configure the sas.logon.saml.providers settings in both the M-T provider and the marketing tenant.
SAS Viya 2021.2.4 Bypass SAS Logon Manager
Prior to the SAS Viya 2021.2.4 release, SAS provided a sample patch transformer to update the SAS Logon Manager Ingress definition. This patch transformer used a server snippet annotation to insert a login_hint into requests. Adding the login_hint allowed customers using SAML or OpenID Connect to bypass SAS Logon Manager, meaning that end-users would automatically get redirected to the third-party SAML or OIDC Identity Provider (IdP). However, an issue with custom snippets was discovered, as documented in CVE-2021-25742. With SAS Viya 2021.2.4 the sample patch transformer has been removed and SAS is providing a configuration option to enable bypassing SAS Logon Manager. In this post, we discuss this updated approach for bypassing SAS Logon Manager.